Quickstart
Install Qovery on your AWS account in less than 30 minutes. Qovery will create a Kubernetes cluster for you and manage it for you. To install Qovery on an existing Kubernetes cluster, please refer to the dedicated documentation.
Before you begin, this page assumes the following:
- You have an account and an Organization on Qovery
- You have an AWS account
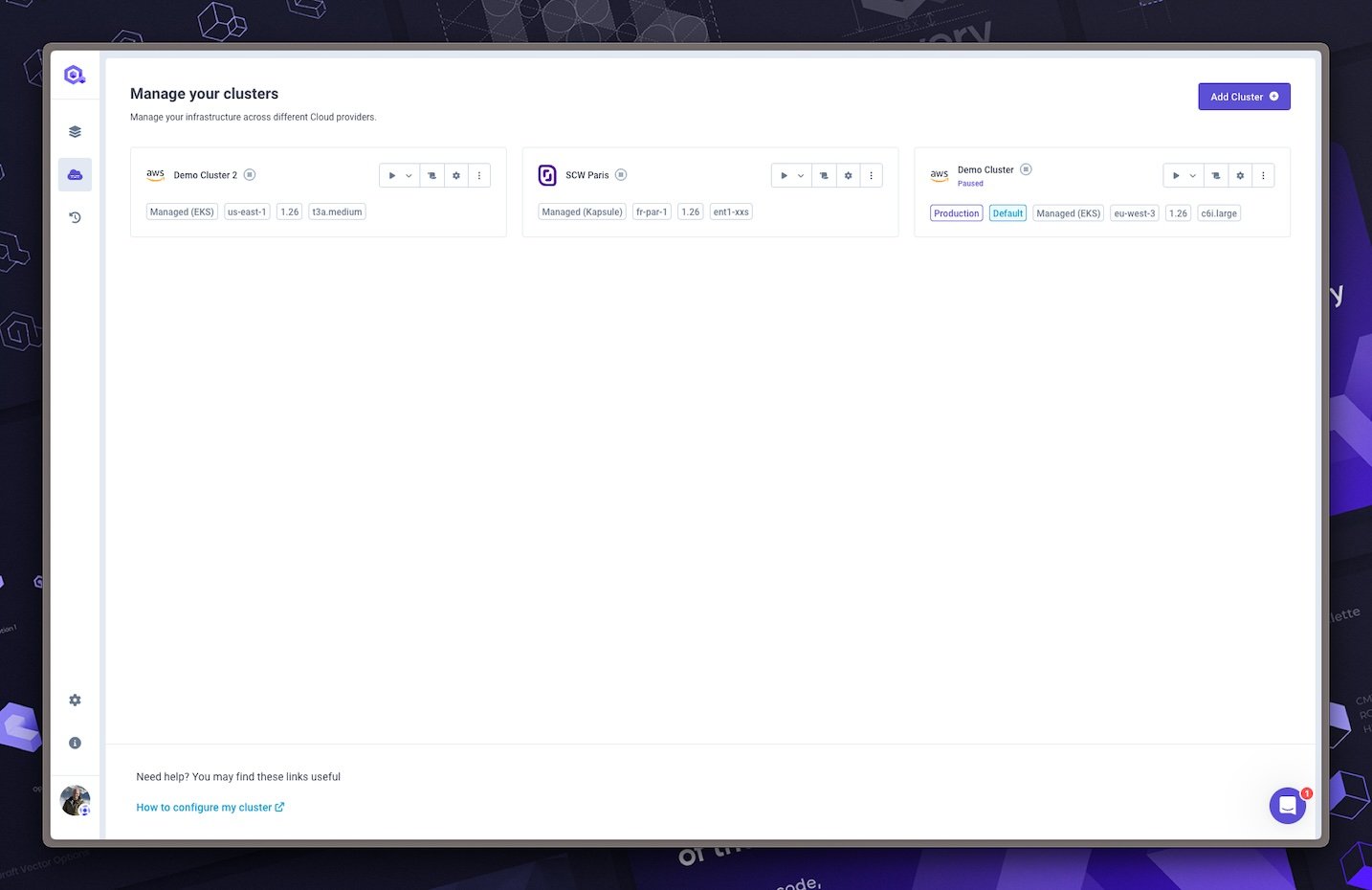
Create a Kubernetes cluster
Now you can create your Kubernetes cluster. Follow this guide to create your Kubernetes cluster.
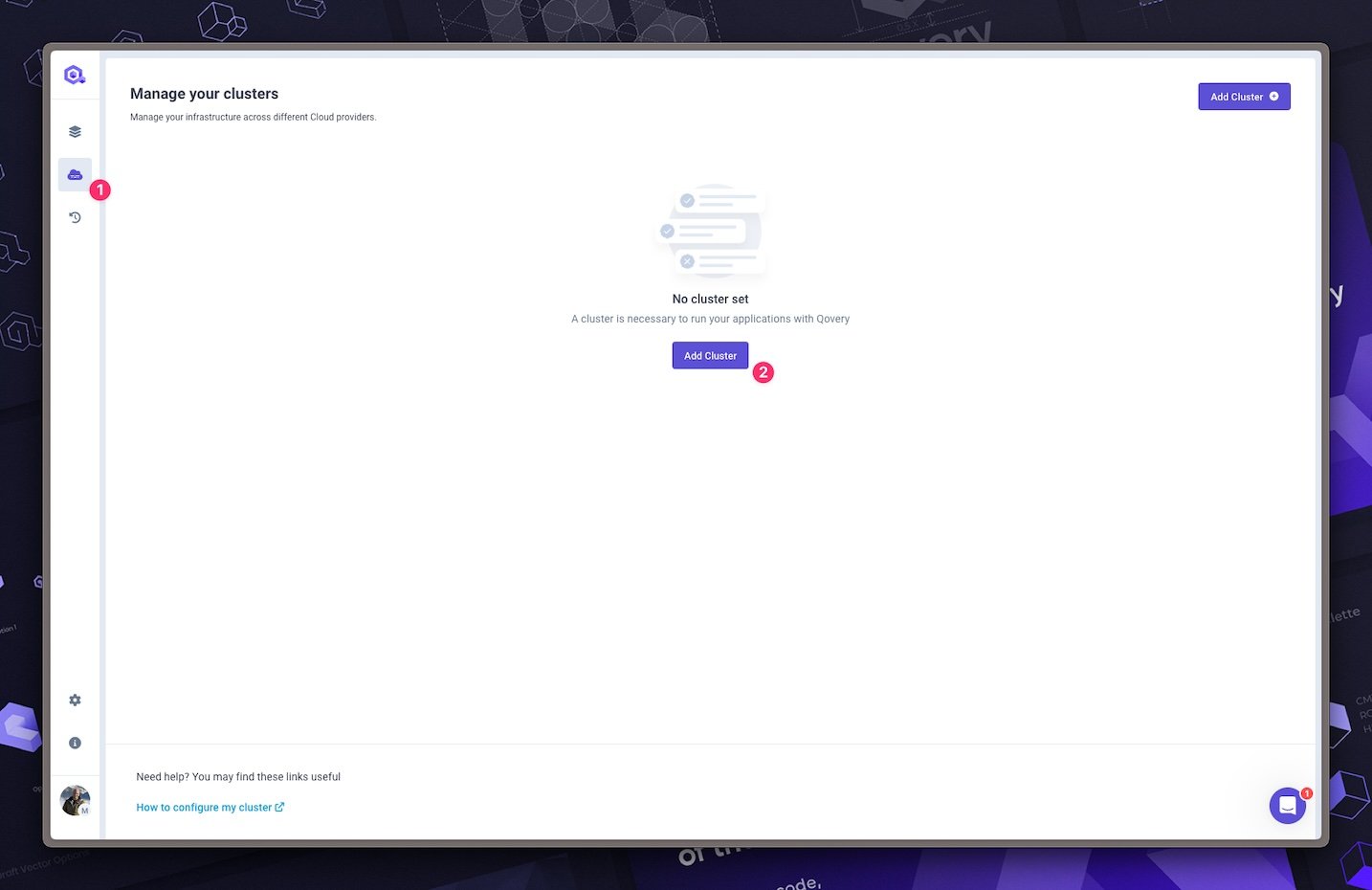
Note that you can create multiple clusters on the same AWS account with different VPCs. You can also create multiple clusters on different AWS accounts. Qovery will manage them for you.
Attach AWS credentials
Follow this guide to create your AWS credentials.
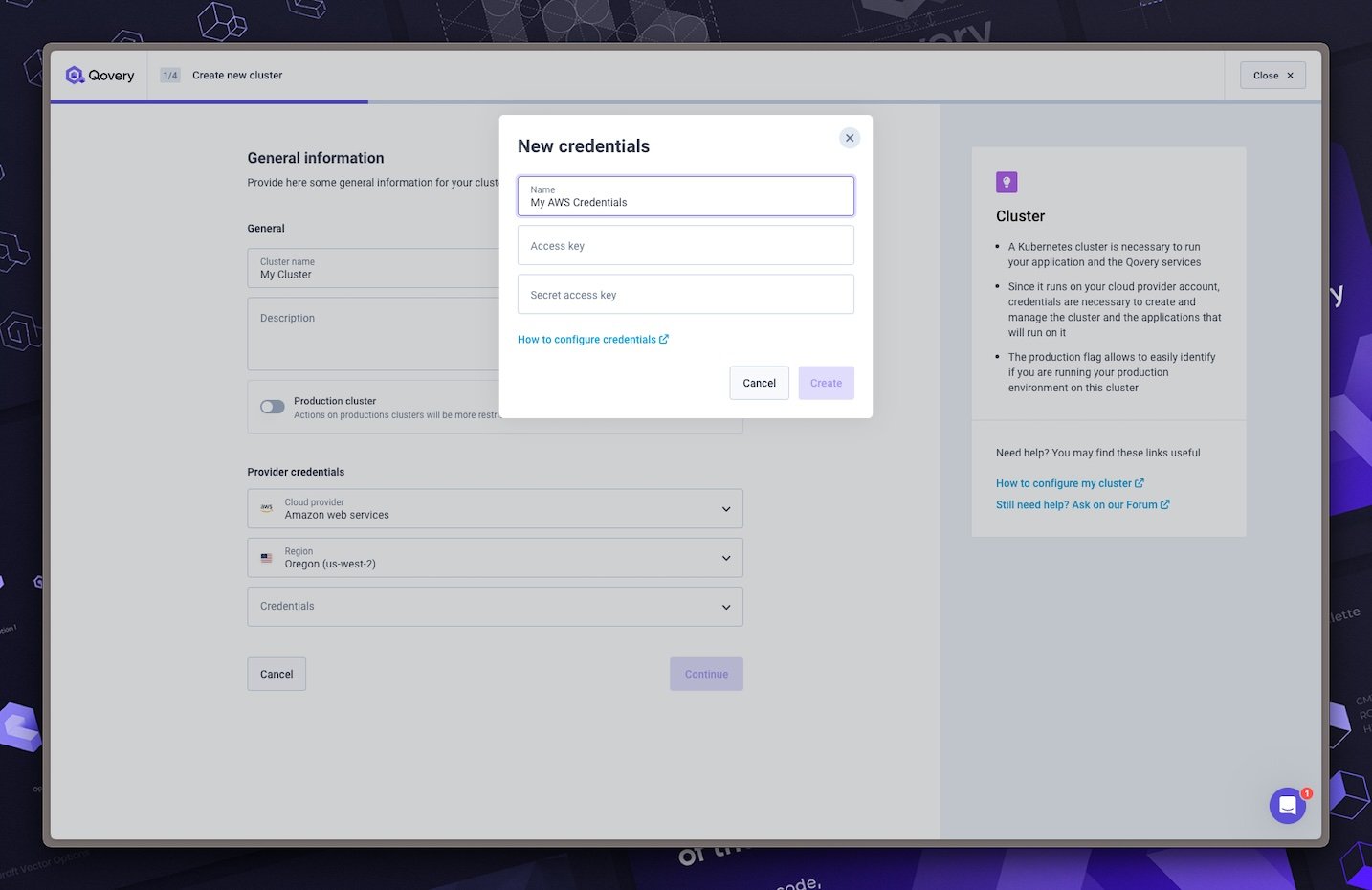
Then attach your credentials to your cluster and click on
Create. Then, click onContinue.Select your options
Qovery propose multiple options that you can select to customize your installation. You can also change some of them later.
Install Qovery
Click on
Create and Deployto create the cluster and install Qovery on it.It will take up to 30 minutes to create the cluster, VPC and install Qovery on it. But you can already configure your first application.
You should see your new cluster in the list of clusters.