Creating a sub-account on AWS is a great way to manage multiple projects and resources. It allows you to separate resources, billing, and access control. However, managing multiple accounts can be cumbersome. Single Sign-On (SSO) is a great way to manage multiple accounts and resources.
In this guide, you will learn how to configure Single Sign-On (SSO) for a sub-account in AWS with Qovery. Then it's convenient to switch between accounts. Here is an example of what it looks like with 5 different accounts:
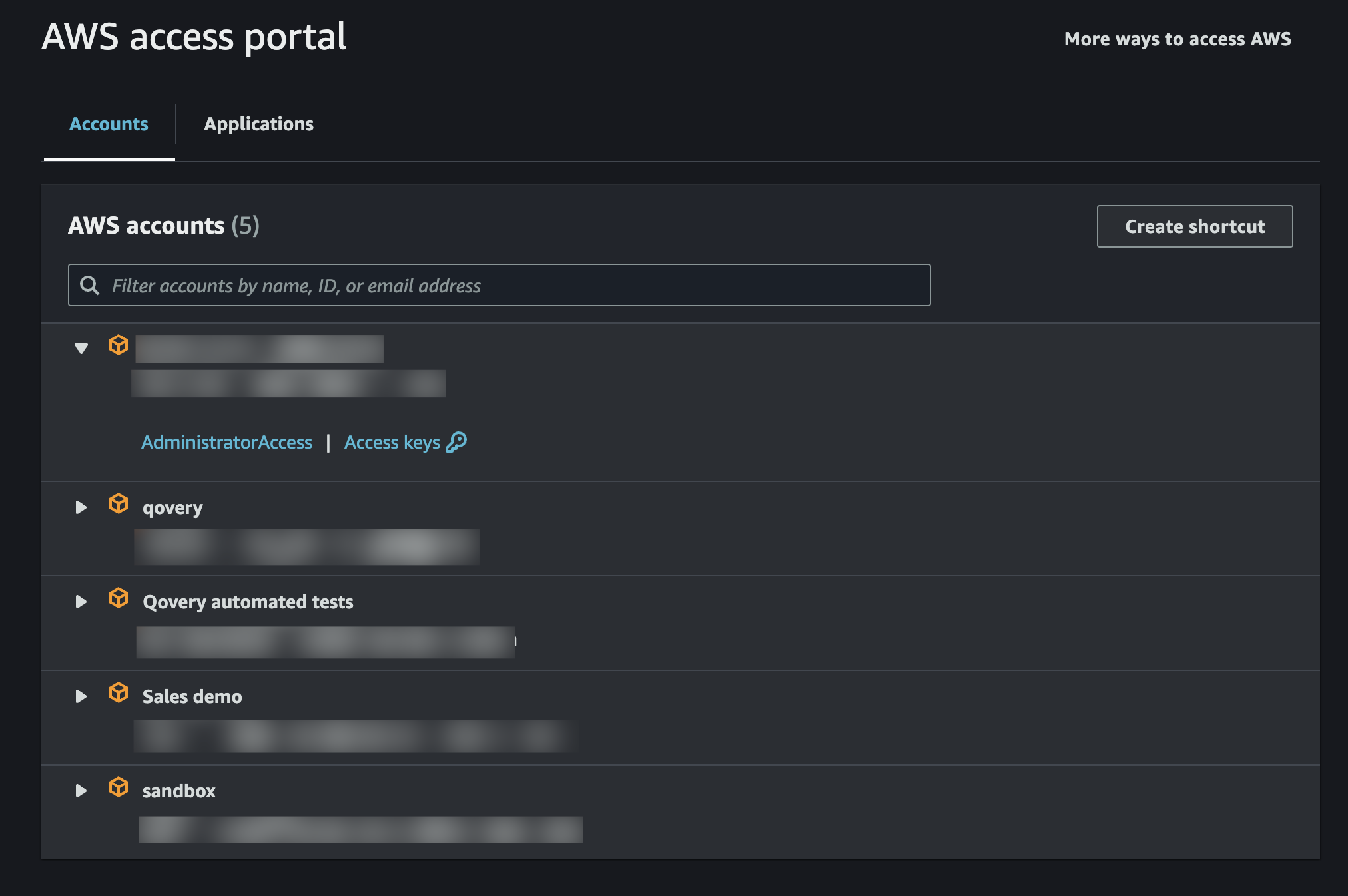
Create a subaccount in AWS
On your AWS master account, go to the AWS Management Console, and click on the My Account top right dropdown menu.
Then, click on AWS Organizations, and click on Add an AWS account:
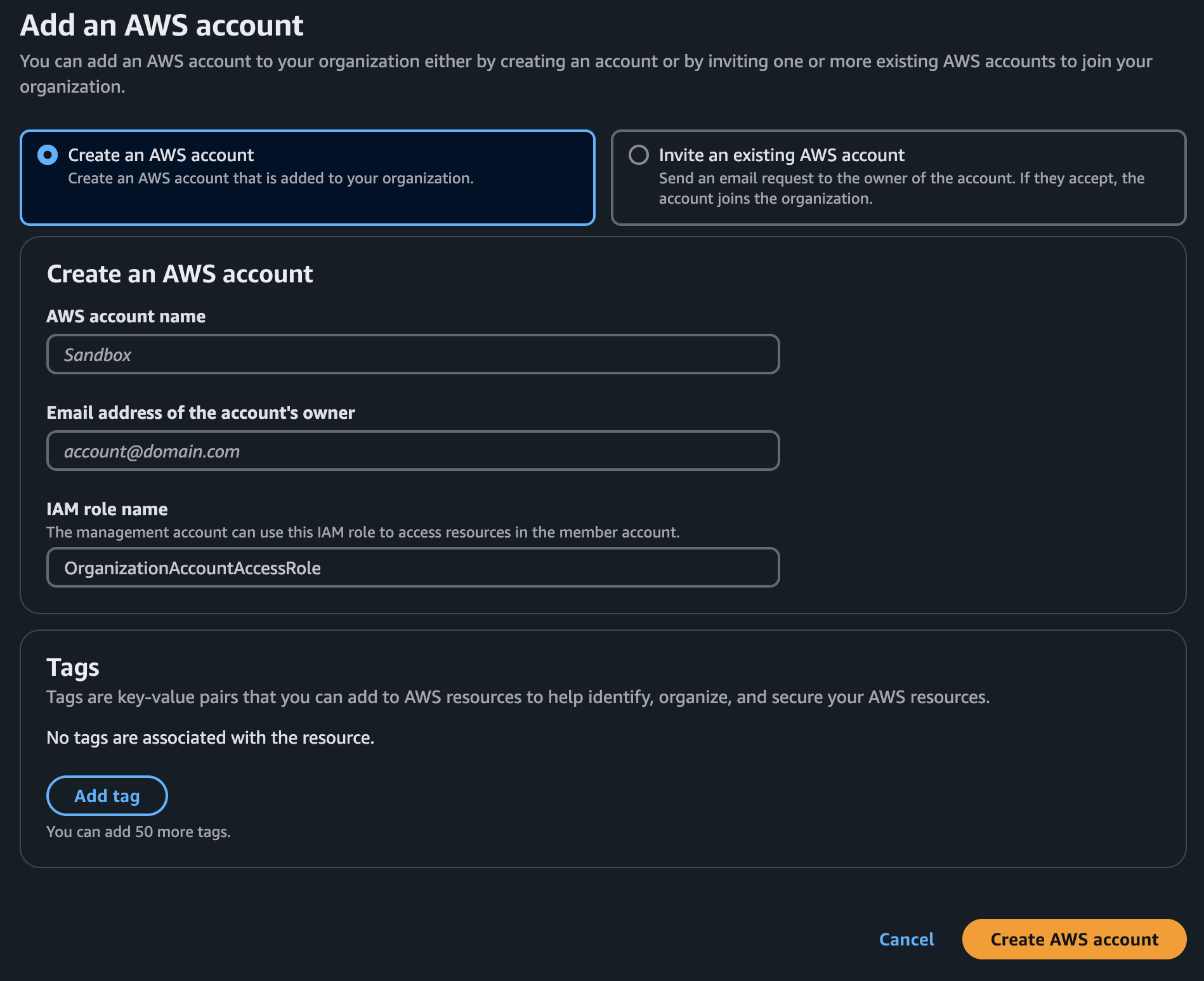
If all goes well, this takes us back to the list of accounts. If the new one looks grayed out, it’s not quite done being created; wait a little and refresh the list until it looks normal. Log out of the master account, and connect to this account.
Configure SSO on AWS for the sub-account
You will find in this guide, how to configure SSO on your subaccount with your identity provider (Google Workspace, Okta, Microsoft Active Directory etc.).
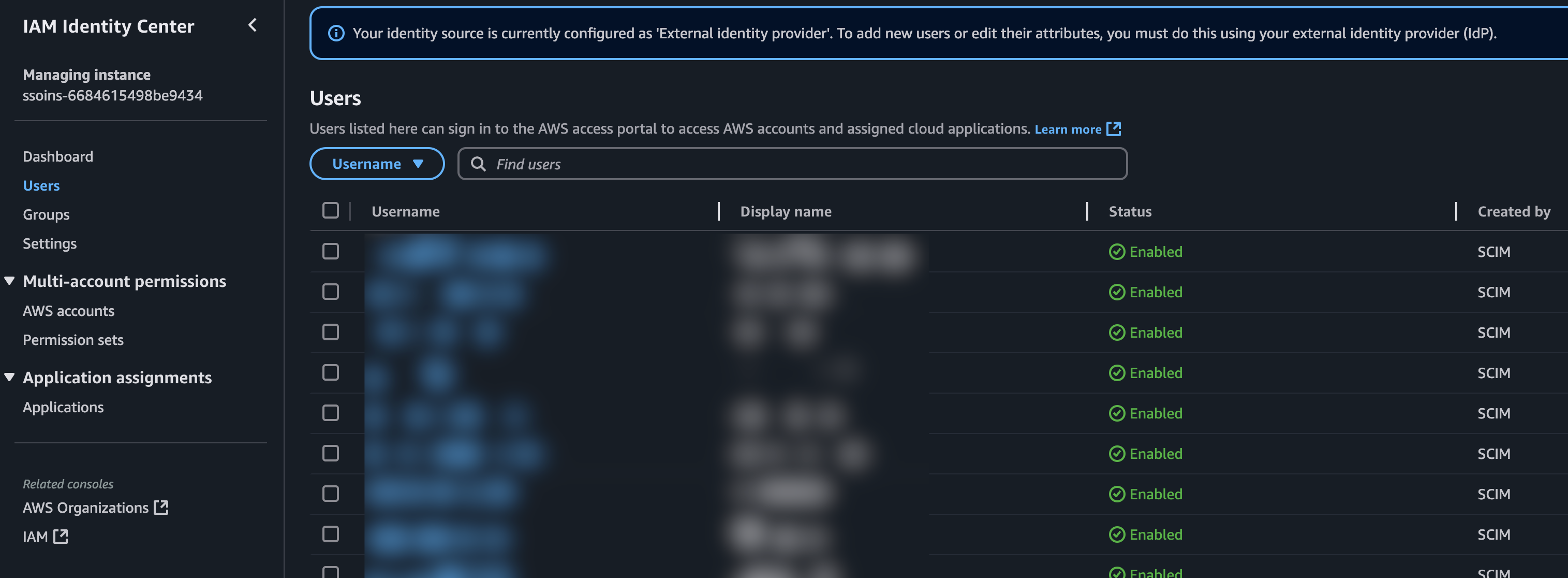
In the ends, you should see your users in the AWS IAM Identity Center console:
Ass SSO (with Qovery) on your EKS cluster to support SSO (optional)
Qovery allows you to connect to your EKS cluster using SSO. It's optional, but if you want to do this anyway, please refer to this guide.
SSO sync for Google workspace (optional)
SSO Sync is helping you populate AWS SSO directly from your Google Workspace users. It's optional, you can use it inside Qovery with a Dockerfile (clone the repo and add this Dockerfile, feel free to update to your needs):
FROM debian:stable-slimRUN apt-get update && apt-get -y install curl && apt-get clean &&\curl -Lo ssosync.tgz https://github.com/awslabs/ssosync/releases/download/v2.0.2/ssosync_Linux_x86_64.tar.gz &&\tar -xzf ssosync.tgz -C /tmp &&\cp /tmp/ssosync /usr/bin/ &&\chmod 755 /usr/bin/ssosync &&\rm -Rf ssosync.tgz /tmp/*ENTRYPOINT ["/usr/bin/ssosync"]
Then you can try to run it. For example, to sync users from Google Workspace to AWS SSO:
docker run -t $(AWS_SSO_SCIM_API_ACCESS_TOKEN) -e $(AWS_SSO_SCIM_API_ENDPOINT) -u $(GOOGLE_WORKSPACE_ADMIN_USER_EMAIL) -c $(GOOGLE_WORKSPACE_CREDENTIALS_FILE) -g $(GOOGLE_WORKSPACE_GROUPS) --log-level debug -r $(AWS_REGION) -i $(AWS_SSO_SCIM_IDENTITY_STORE_ID)
You should see something like:
time="2024-12-18T14:30:00Z" level=info msg="Syncing AWS users and groups from Google Workspace SAML Application"time="2024-12-18T14:30:00Z" level=info msg=syncing sync_method=groupstime="2024-12-18T14:30:00Z" level=info msg="get google groups" query="name:sso* email:sso*"time="2024-12-18T14:30:01Z" level=debug msg="preparing list of google users and then google groups and their members"...time="2024-12-18T14:30:26Z" level=info msg="sync completed"