Maintenance
This guide will provide inputs about maintenance with Qovery. Qovery provides automatic and silent updates as much as possible. With and without cloud providers.
Kubernetes and components, patches, and upgrades
Qovery manages Kubernetes updates through the Cloud provider update mechanism and ensures full compatibility with all deployed infrastructure components (Nginx ingress, cert-manager, CNI, CSI, etc.) inside the Kubernetes cluster.
Security patches and minor updates are applied automatically and silently by the cloud provider. Kubernetes major updates are applied automatically by Qovery to ensure compatibility between every deployed components inside the cluster.
Managed services patches and upgrades
By default, every managed service deployed by Qovery is configured with automatic patches and upgrades proposed by the cloud provider.
Major version upgrades are up to the end user to decide when it's the right time to upgrade.
Cloud providers' limits
Cloud providers are using quotas for various reasons. Some of them are to prevent abuse, some others are to prevent overloading the infrastructure, and others are to prevent an excessive bill.
It occurs that some customers are reaching the limits of their cloud provider. In this case, Qovery gives the information in the infrastructure or applications logs.
It is up to the customer to contact the Cloud provider via ticketing support to increase the limits.
Rotating system credentials
Some customers want to rotate their system credentials because on legal requests, security requirements, or other reasons. Qovery provides makes it simple to rotate credentials.
Here is the way we recommend to avoid any downtime on your cluster and for your application deployments. Open your AWS console and open the Qovery user in the IAM service.
Click on the Security credentials tab, you will see one access key present:
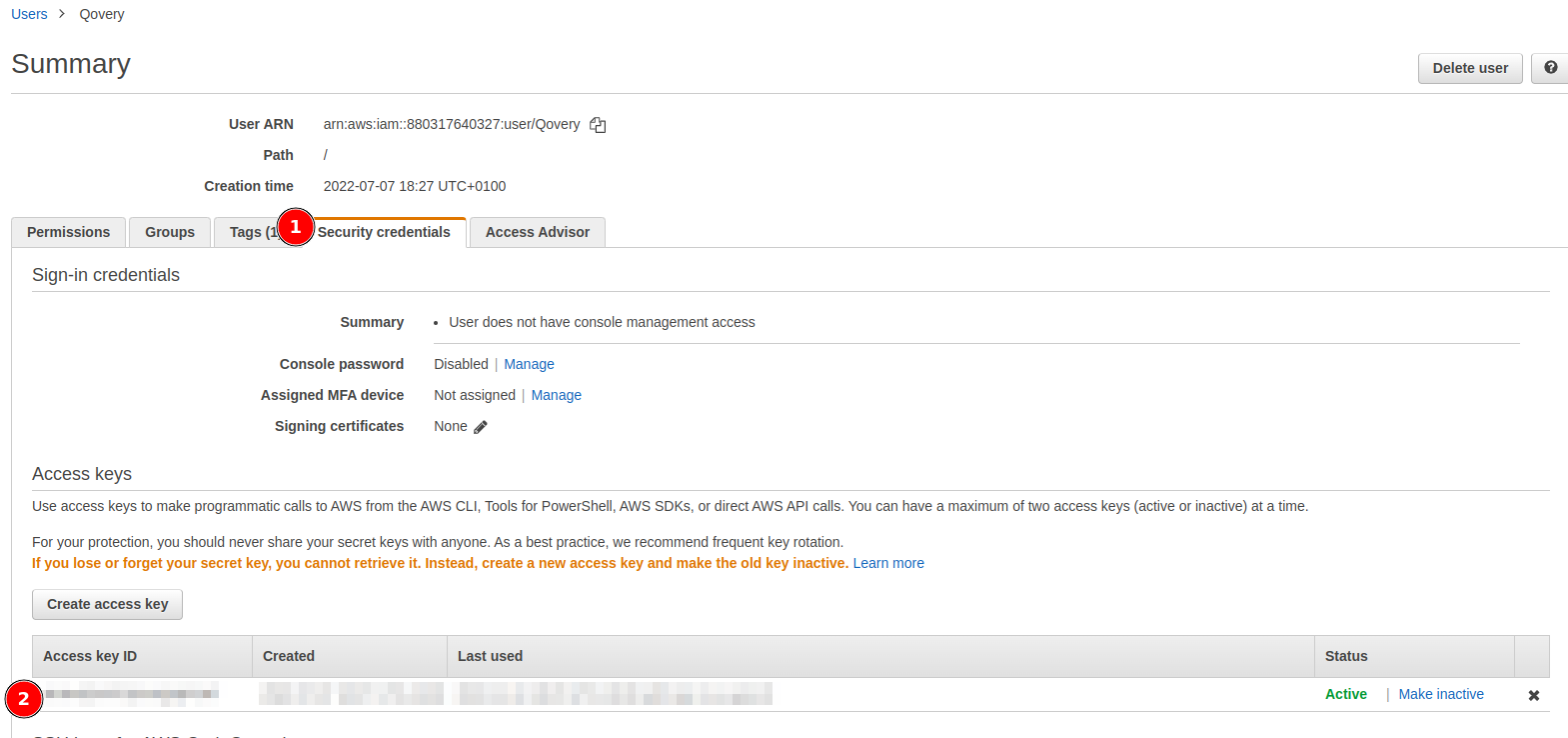
For a single account, we can create up to two access keys. So we can create a new one, request a cluster deployment, wait for the deployment to be done, and then delete the old one.
You can now 2 ways to rotate your credentials, select the one you prefer:
- Manual: you update manually credentials from the Qovery interface
- Automatic: you update automatically credentials with a script
Manual rotation
You can update or rotate manually credentials on your AWS account this way:
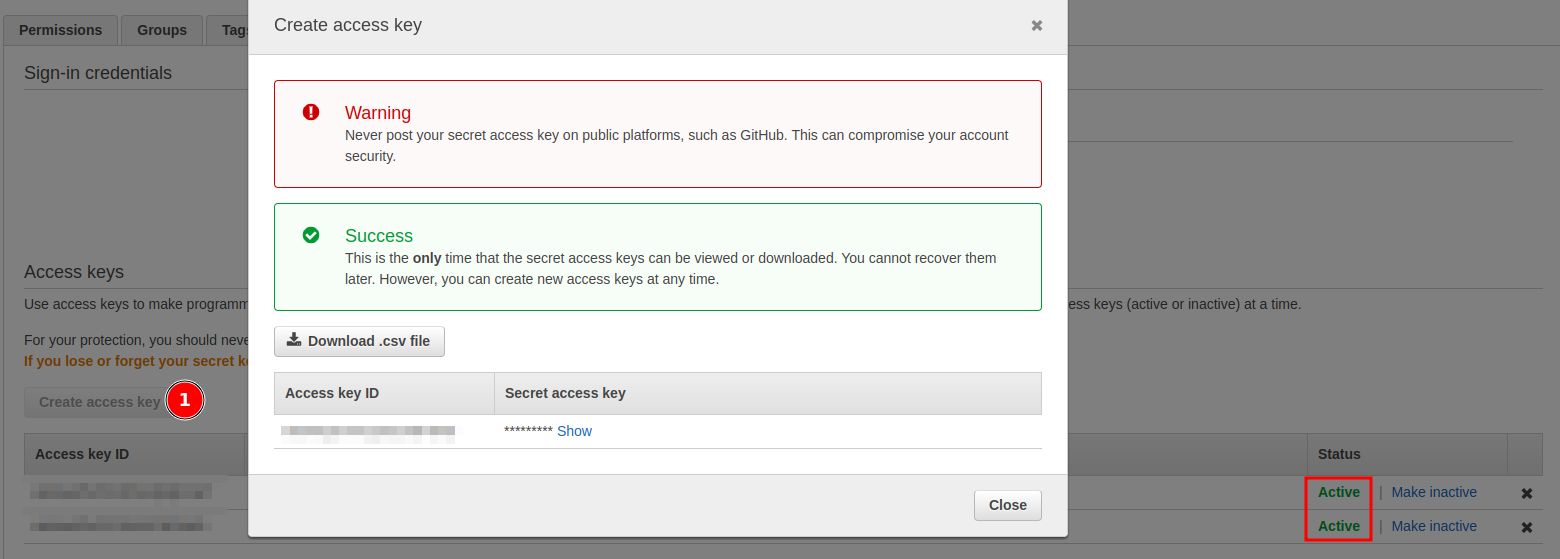
- Click on the
Create access keybutton - Save the
access keyandsecret access Keyin a safe place - Go to your Qovery dashboard to update the credentials on Qovery console.
Deploythe cluster once again to apply changes- Once the cluster is fully updated, wait 2h (to ensure all ongoing deployments are done)
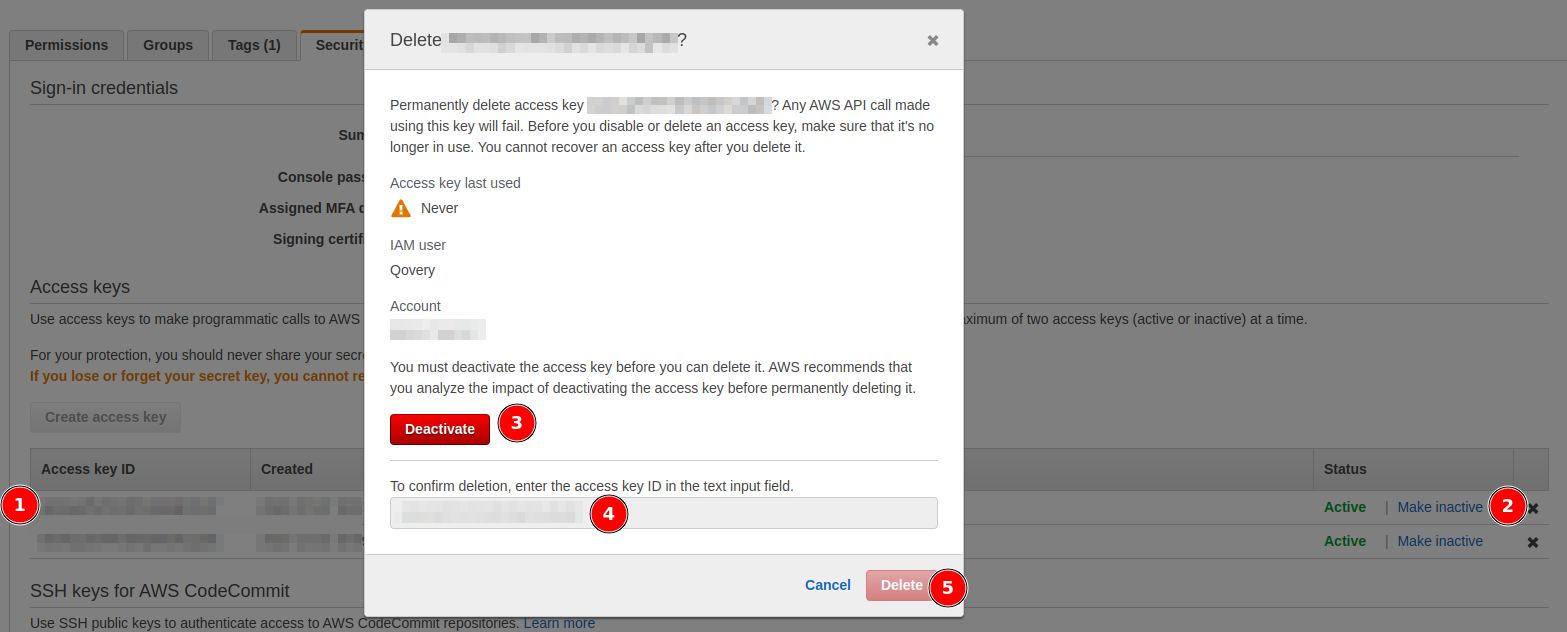
- Delete the old access key from the AWS console:
Automatic rotation
Another way to do it more programmatically. Here is a script to perform those actions, adapt it to your needs if you need and add it to your
#!/bin/bash############## VARIABLES AND INSTRUCTIONS ############### Ensure you have jq and awscli installed# 1. Ensure your AWS environment variables are set: https://docs.aws.amazon.com/cli/latest/userguide/cli-configure-envvars.html# 2. AWS username to perform the rotationaws_iam_username="Qovery"# 3. Use qovery CLI to generate a dedicated tokenqovery_token="xxx"# 4. Organization ID can be retrieved inside the Qovery console URL, where your cluster is locatedorganization_id="xxx"# 5. Get your credentials: curl -s -X GET -H "Content-type: application/json' -H 'Authorization: Token $qovery_token" "https://api.qovery.com/organization/$organization_id/aws/credentials"credentials_id="xxx"# 6. Name of the credentials to updatecredentials_name="My organization credentials"# 7. Cluster ID can be retrieved inside the Qovery console URL, where your cluster is locatedcluster_id="xxx"# 8. Set the delay to wait before deleting the old key in seconds (do not go below 7200)delay_before_delete_old_key=7200############## DO NOT EDIT ##############set -eecho "[+] Ensure there is only one Access Key"old_aws_access_key=$(aws iam list-access-keys --user-name $aws_iam_username | jq -r '.AccessKeyMetadata[].AccessKeyId')if [ $(echo $old_aws_access_key | grep -c ' ') -ne 0 ]; thenecho "ERROR: more than one access key found, please delete the one not used by Qovery"exit 1fiif [ "$old_aws_access_key" == "" ] ; thenecho "ERROR: no access key found, are you sure it's the correct user?"exit 1fiecho " -> Current (future old) key detected: $old_aws_access_key"current_time=$(date +"%s")max_time=$((current_time + delay_before_delete_old_key))cluster_status=""echo "[+] Create a new Access Key"new_aws_access_key_json=$(aws iam create-access-key --user-name $aws_iam_username)new_aws_access_key=$(echo $new_aws_access_key_json | jq -r '.AccessKey.AccessKeyId')new_aws_secret_key=$(echo $new_aws_access_key_json | jq -r '.AccessKey.SecretAccessKey')echo " -> Successfully created a new access key: $new_aws_access_key"echo "[+] Update Qovery credentials"curl -s -X PUT -H "Content-type: application/json" -H "Authorization: Token $qovery_token" -d "{\"name\": \"$credentials_name\", \"access_key\": \"$new_aws_access_key\", \"secret_key\": \"$new_aws_secret_key\"}" "https://api.qovery.com/organization/$organization_id/aws/credentials/$credentials_id" 1>/dev/nullecho "[+] Deploy the cluster with the new credentials"curl -s -X POST -H "Content-type: application/json" -H "Authorization: Token $qovery_token" "https://api.qovery.com/organization/$organization_id/cluster/$cluster_id/deploy" 1>/dev/nullecho "[+] Wait for the cluster deployment to be done"sleep 15while [ "$cluster_status" != "RUNNING" ]; dosleep 60cluster_status=$(curl -s -X GET -H "Content-type: application/json" -H "Authorization: Token $qovery_token" "https://api.qovery.com/organization/$organization_id/cluster/$cluster_id/status" | jq -r '.status')echo " -> $(date "+%H:%M") Waiting for the cluster deployment to be done. Current status: $cluster_status..."# Ensure the cluster is in a valid stateif [ "$cluster_status" != "DEPLOYMENT_QUEUED" ] && [ "$cluster_status" != "DEPLOYING" ] && [ "$cluster_status" != "DEPLOYED" ] && [ "$cluster_status" != "RUNNING" ]; thenecho "ERROR: the cluster does not have a correct status, please check cluster logs and fix the issue. Then delete the key $old_aws_access_key and retry"exit 1fiif [ $(date +"%s") -gt $max_time ]; thenecho "ERROR: timeout reached, the cluster is not deployed yet, please check cluster logs and fix the cluster issue. Then delete the key $new_aws_access_key and retry"exit 1fidoneecho "[+] Waiting up to 2h to ensure all ongoing deployments are done ($(date -d @$max_time))"while [ $(date +"%s") -lt $max_time ]; dosleep 10doneecho "[+] Delete the old Access Key"aws iam delete-access-key --access-key-id $old_aws_access_key --user-name $aws_iam_usernameecho "[+] Done"
You will see the following output:
[+] Ensure there is only one Access Key-> Current (future old) key detected: xxx[+] Create a new Access Key-> Successfully created a new access key: yyy[+] Update Qovery credentials[+] Deploy the cluster with the new credentials[+] Wait for the cluster deployment to be done-> 15:04 Waiting for the cluster deployment to be done. Current status: DEPLOYING...-> 15:05 Waiting for the cluster deployment to be done. Current status: DEPLOYING...-> 15:06 Waiting for the cluster deployment to be done. Current status: DEPLOYING...-> 15:07 Waiting for the cluster deployment to be done. Current status: RUNNING...[+] Waiting up to 2h to ensure all ongoing deployments are done (Fri Nov 11 03:22:57 PM CET 2022)[+] Delete the old Access Key[+] Done